OSPF Router-id – 32-bit unique identifier of OSPF processes running on the router. OSPF process router-id selection criteria:
- Use the router ID configured with router-id command in router process
- Uses the highest non-shutdown ipv4 loopback address
- Use the highest non-shutdown ipv4 configured interface address
-Multiple OSPF processes will skip addresses used by other OSPF processes on the device
-The RID configured with the router-id command will never change. A RID acquired by the process picking an interface address will change if the process restarts and the previous criteria has changed.
-The RID can be changed with either the router-id command, or altering interface addresses or states. Then restarting the OSPF process with the clear ip OSPF process exec command.
OSPF Messages
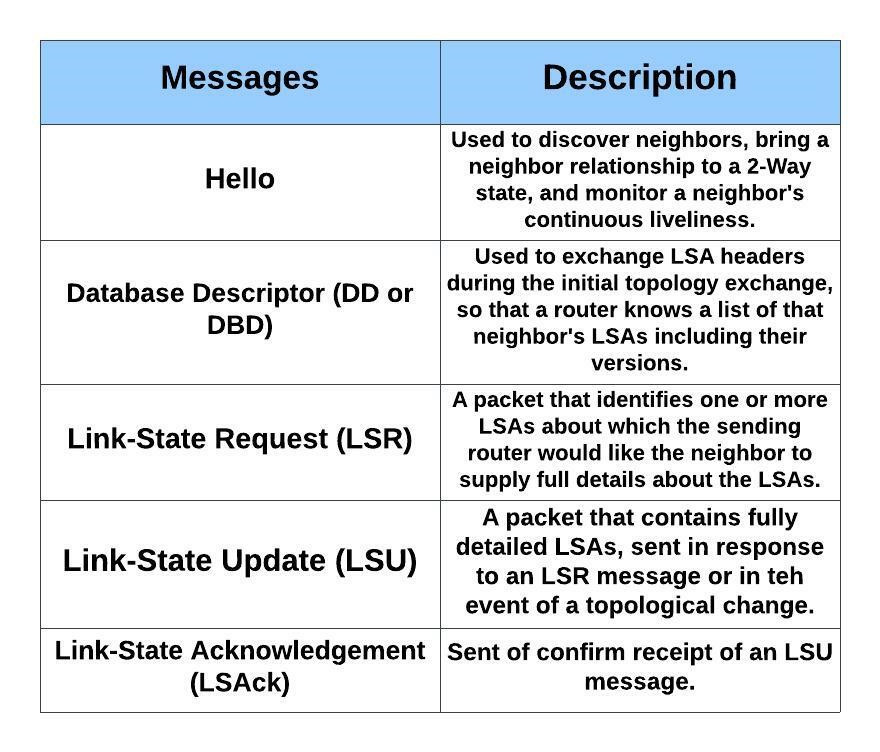
-LSAs are not OSPF messages. An LSA is a data structure, held inside a router’s LSDB and exchanged inside LSU messages.
OSPF Neighbor States
-Neighbors – Two routers that share a common data link and that exchange hello messages, and the hellos must match for certain parameters. (2-way/Drother)
-Adjacent (Fully Adjacent) – Two neighbors that have completed the process of fully exchanging DD and LSU packets directly between each other. (DR/BDR)

-Hello messages, 224.0.0.5/FFO2::5/ALLSPFROUTERS, 224.0.0.6/FF02::6/ALLDESIGNATEDROUTES
- Discover other OSPF-speaking routers on common subnets
- Check for agreement on selected configuration parameters
- Verify bidirectional visibility between routers
- Monitor health of the neighbors to react if the neighbor fails
- Hellos are sourced from primary IP address on the enabled interface
-Hello Message Parameter Checks
- Authentication must match
- Subnet mask must match
- Area must match
- Area type must match
- RIDs must be unique
- Hello and Dead Timers must match
-MTU mismatch would affect database synchronization in the ExStart and Exchange phases. Routers can still become 2-Way neighbors successfully.
-Nat can affect this as well. If you run into issues check the range of your Nat statement.

Designated Router – DR/BDR
The DR/BDR are responsible for the flooding of LSUs. On a multi-access segment all routers are Fully adjacent with the DR & BDR. The DR also generates type 2 LSAs which represents the subnet and the router interfaces connected to the subnet.
Criteria for DR/BDR election:
- Interface OSPF priority of 1-255 (0 excludes the router interface from participating in a DR/BDR election).
- Highest router-id
-The DR/BDR position cannot be preempted. For instance, if a router is added to the segment with a higher router-id or priority. Current DR/BDR would have to be reset for another election to take place. If the DR goes down the BDR takes over. Then an election for a new BDR would be held.
– On multi-access segments, updates are sent to 224.0.0.6. Then the DR floods the LSUs with updated LSAs within the area. The LSU flooded by the DR serves as an acknowledgment to the original sending router that it was received. All routers except the originating router will acknowledge the flooded LSU with a unicast LSAck to the DR.
OSPF Network Types
-Broadcast Multi-access: Broadcast networks are capable of connection more than two devices. Broadcasts sent out one interface are capable of reaching all devices on the segment.
Router(config-if)# ip ospf network broadcast
-Non-Broadcast Multi-access: Frame Relay, ATM, and X.25 are considered non-broadcast multi-access, in that they can connect more than two devices, and broadcasts sent out one interface might not always be capable of reaching all the interfaces attached to a segment.
Router(config-if)# ip ospf network non-broadcast
-Point-to-Point: Allows only two devices to communicate. Point-to-Point circuits do not use ARP, and broadcast traffic does not become the limiting factor. Default for serial interfaces (HDLC or PPP encapsulation), GRE and Point-to-Point frame relay subinterfaces.
Router(config-if)# ip ospf network point-to-point
-Point-to-Multipoint: Not enabled by default on any medium. Supports hub-and-spoke connectivity while using the same IP subnet and is commonly found in frame relay and L2VPN topologies. Interfaces enabled for OSPF point-to-multipoint, add the interface’s IP to the LSDB as /32. Routes advertised out that interface will change the next-hop to the interfaces IP address.
Router(config-if)# ip ospf network point-to-multipoint
-Loopback: Can only be used on loopback interfaces. This network type indicates the address will always be advertised as a /32 prefix length. Changing the network type on the interface changes this behavior. The loopback network type cannot be manually assigned.

LSA TYPES
- Router – One per router, per area, listing the router’s RID and all interface IP address in that area. Represents stub networks as well. Flooded only within its area of origin.
- Network – One per transit network. Created by the DR on the subnet, and represents the subnet and the router interfaces connected to the subnet. Flooded only within it are of origin.
- Net Summary – Created by ABRs to represent networks present in one are when being advertised into another are. Defines the subnets in the origin are, and cost, but no topology data. Flooded only within its area of origin; re-originated on ABRs.
- ASBR Summary – Like a type 3 LSA, except it advertises a host route used to reach an ASBR. Flooded only within its area of origin; re-originated on ABRs.
- AS External – Created by ASBRs for external routes injected into OSPF. Flooded to all regular areas.
- Group Membership Defined for MOSPF, not supported by Cisco IOS.
- NSSA External – Created by ASBRs inside an NSSA, instead of a type 5 LSA. Flooded only within its area of origin; converted to type 5 LSA on an ABR toward other areas.
- External Attributes – Created by ASBRs during BGP-to-OSPF redistribution to preserve BGP attributes of redistributed networks. Not implemented in Cisco routers.
9-11. Opaque – Used as generic LSAs to allow for easy future extension of OSPF; for example, type 10 has been adapted for MPLS traffic engineering. These LSAs have different flooding scope: Type 9 has link-local flooding scope, type 10 has area-local flooding scope, type 11 has autonomous system flooding scope equivalent to the flooding scope of type 5 LSAs ) not flooded into stubby areas and NSSAs).
Router Types:
- ABR: Arouter that has one interface in area 0 and other interfaces in non-zero areas. The ABR can filter routes, as well as summarize routes. Routers in an area have a complete view of the area. As they have identical LSDBs for that area. The ABR is responsible for flooding type 3 LSAs into the area.Two important rules in OSPF ABR functionality:
- Only intra-area routes are translated into type 3 LSAs and flooded into the backbone area. Both intra-area and inter-area routes from the backbone are translated into type 3 LSAs, then flooded to non-backbone areas.
- When an ABR runs SPF algorithm it ignores all type 3 LSAs received from non-backbone areas. This ensures that an ABR does not traverse a non-backbone area to reach a network that is located in the backbone or in some other non-backbone area.
- ASBR: A router that injects routes originating outside the OSPF domain. ASBRs are also a point of filtering and summarization for injected routes. A router can be both an ASBR and ABR. Ex- A router injects a default route. (In normal areas, an injected default route is a type 5 LSA)
Area Types:
- Normal Area: Allows the flooding of all LSA types.
- Backbone Area: A special area that all ABRs must connect to. Type 3 LSAs must pass through this area to be accepted by a non-originating ABR.
- Stub Area: A area the does not allow the propagation of type 5 LSAs. A default route is injected as a type 3 LSA by the ABR.
- Totally Stubby Area: A area that does not allow the propagation of type 3, 4, and 5 LSAs. Only exception is the default route injected by the ABR as a type 3 LSA.
- NSSA Area: A area that does not allow type 5 LSAs. External routes are injected as type 7 LSAs. No default route is injected without additional configuration. Default route injected is an type 7 LSA. Area <#> nssa Default-information originate
- Totally NSSA Area: A area that does not allow type 3&5 LSAs. External routes are injected as type 7 LSAs. A default route is injected as a type 3 LSA by the ABR.
Authentication:
OSPF supports four types of authentication:
- None: no authentication used
- Clear text: clear text passwords used
- MD5: Uses MD5 algorithm to hash password
- SHA: Uses SHA algorithm with key-chain to hash password
Note: IOS 15.4(1) supports the extended SHA-HMAC (RFC 5709)
Default-Route:
The OSPF router command default-information originate will propagate a default route through the OSPF domain. Without the keyword always, a default route must be present in the routing table.
The default route is advertised as an external type-2.
Path Preference:
OSPF uses cost, reached by calculating bandwidth along a path. That is the primary decision in factoring the shortest path. As a loop prevention feature, OSPF also uses these criteria for path preference. Listed from most preferred to least:

- Intra-area routes ( routes learned within the area )
- Inter-area routes ( routes learned from another area)
- External routes type-1 & type 2 ( routes redistributed from another routing domain)
- NSSA routes type-1 & type 2 ( routes redistributed from NSSA area )
These path preferences do not account for cost.
Filtering:
Since OSPF is a link state protocol, all LSDB’s in an area have to be identical. A type 3 LSA can be filtered at the ABR, type 5 or type 7 can be filtered at the ASBR. Filtering on the local router is limited to the routing table.
-Note: To filter type 5 or 7 LSA’s not at the ASBR. You would need to use redistribution and filter the routes with a route-map. An example of this would be filtering a default route.
Summarizing:
Summarizing routes is also accomplished at the ABR & ASBR’s, which also allows for the non advertisement of routes. The biggest advantage of summarizing is smaller routing tables. Allowing for faster SPF calculations. The metric can either be designated or will be the lowest metric of the component routes.
The last note to bring up is that all areas must connect to area 0. All traffic must traverse through area 0. So when creating an OSPF topology this must be taken into account. Using virtual links or GRE tunnels are band aid solutions to temporarily resolve connectivity issues caused by improper design.
As always thank you for your attention and time.